Abstract
Modern smartphones become an everyday part of our life. Checking emails, browsing the Internet, photographing, navigation are successfully carried out with the help of smartphones. Obviously, this happens because mobile phones have been provided with the useful functions.
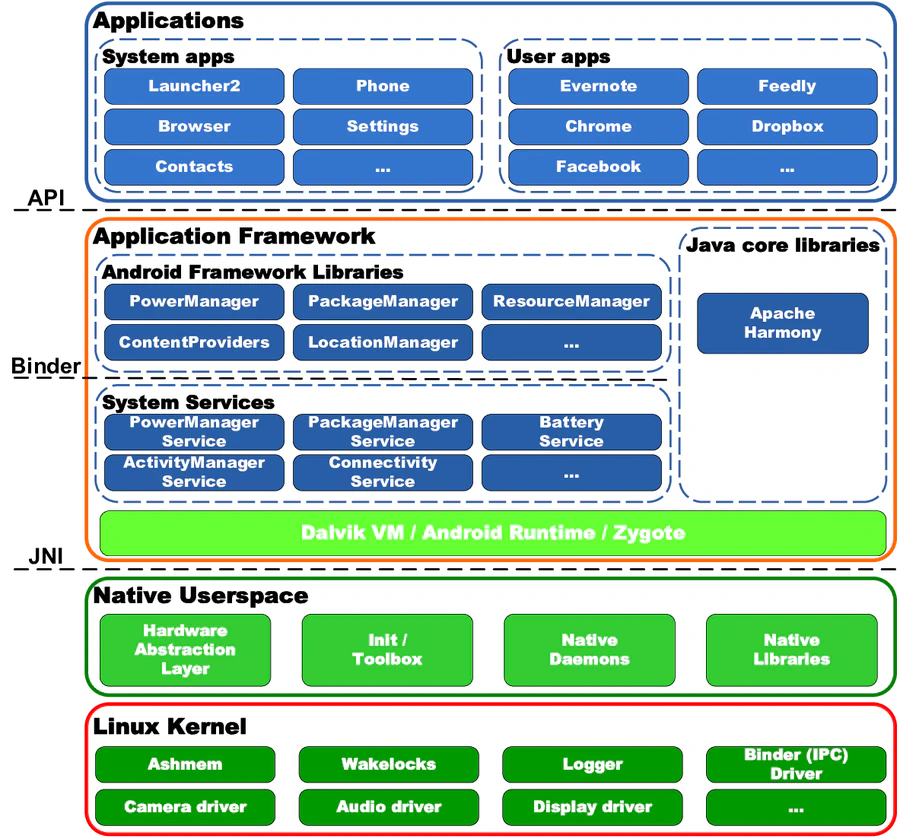
In the smartphone domain, the Android OS is by far the most popular platform being installed on about 79% of all new mobile devices. Those figures clearly show the pervasiveness of Android, mostly justified by its openness. Being a part of the Open Handset Alliance initiative, Google released most of the Android code under open source licences. Thus, we have an ability to explore this operating system, change platform components and build customized images of the Android OS. Moreover, the third-party applications can be easily developed and tested on this platform without publishing them in an application market. Hence, it is not surprisingly why this platform is so popular nowadays.
Unfortunately, the information about the intrinsics of this operating system is sparse and scattered around different resources. This does not concern Android application programming during the last several years lots of books and web resources appeared describing the process and best practices how to develop Android apps. Moreover, the official documentation about app programming is quite complete and can be treated as a credible source of information on that topic. On the contrary, the official documentation about the system programming is poor and gives you good insights about how to download the Android sources and build them. Additional information only partially covers the topics and does not provide you with the whole picture. The situation in case of security is even more dismal.
In this tutorial we try to close the gap. We consider the layered structure of the operating system and examine the main security mechanisms implemented in Android. In particular, we inspect the sandboxing mechanism implemented at the Linux Kernel level. We will consider how the kernel enforces the isolation of applications and operating system components exploiting standard Linux facilities (process separation and Discretionary Access Control over network sockets and filesystem). Further, we plan to consider the security mechanisms implemented at other layers. In particular, we give an understanding how the security is designed at the Android Middleware level. On this level an IPC Reference Monitor mediates all the communications between processes and controls how applications access the components of the system and other apps. In Android, IPC Reference Monitor follows Mandatory Access Control (MAC) access control type and is based on permission system. The implementation details of the permission system is also planned to be considered in the tutorial.
Other notable part of the tutorial is dedicated to the limitations in the Android operating system and the state-of-the-art research approaches that close this gap. In particular, we plan to consider such systems as CRêPE, MOSES, FSquaDRA, etc.