Abstract
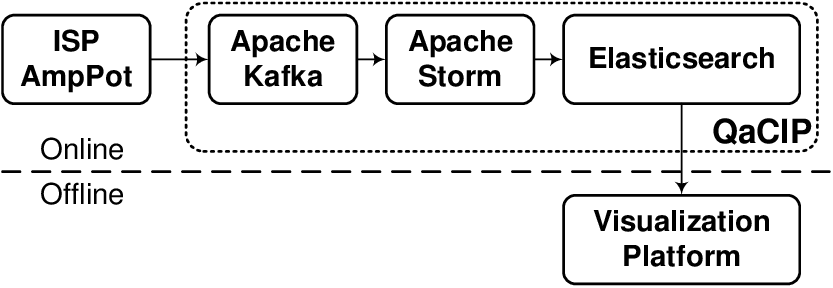
Distributed Reflective Denial of Service attacks (DRDoS) represent an ever growing security threat. These attacks are characterized by spoofed UDP traffic that is sent to genuine machines, called amplifiers, whose response to the spoofed IP, i.e. the victim machine, is amplified and could be 500 times larger in size than the originating request. In this paper, we provide a method and a tool for Internet Service Providers (ISPs) to assess and visualize the amount of traffic that enters and leaves their network in case it contains innocent amplifiers. We show that amplified traffic usually goes undetected and can consume a significant bandwidth, even when a small number of amplifiers is present. The tool also enables ISPs to simulate various rule-based mitigation strategies and estimate their impact, based on real-world data obtained from amplification honeypots.