Abstract
Distributed Reflected Denial of Service (DRDoS) attacks have been continuing to grow unprecedentedly in the recent years. Attackers abuse genuine services running some application protocols built over UDP to generate amplified traffic targeting victim network. An Internet Service Provider (ISP) may host hundreds or even thousands of hosts running these vulnerable protocols that could become amplifier nodes in DRDoS attacks. If abused, they can collectively cause large volumes of garbage amplification traffic flowing out of the ISP network. This wasteful bandwidth consumption costs the provider money and loss of Quality of Service (QoS) to its customers. Moreover, the owners of services vulnerable to amplification have to spend their resources to process illicit requests.
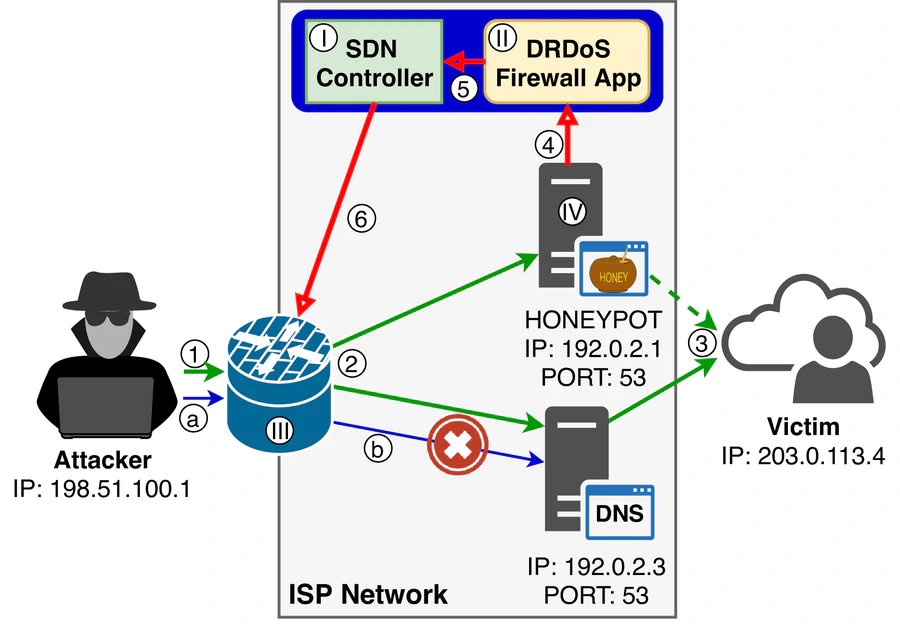
In this paper, we propose a novel idea to filter out garbage traffic from an ISP network. We employ a special type of a honeypot that collects information about ongoing DRDoS attacks, and Software Defined Network (SDN) paradigm offering us a unified interface to deploy firewall rules on a large variety of network devices. The rules block incoming amplification requests from reaching amplifiers located within the provider network rescuing vulnerable services from being abused. This prevents garbage traffic from leaving the network enabling the provider to save money and improve QoS. Moreover, our solution also contributes to victim’s liveliness because it reduces the attack traffic reaching the target network. In addition, it stimulates ISPs to implement ingress filtering best practices for all its network routers in order to minimize damage from an attacker located in the same network.