Methods and Systems for Reducing Unwanted Data Traffic in a Computer Network
Abstract
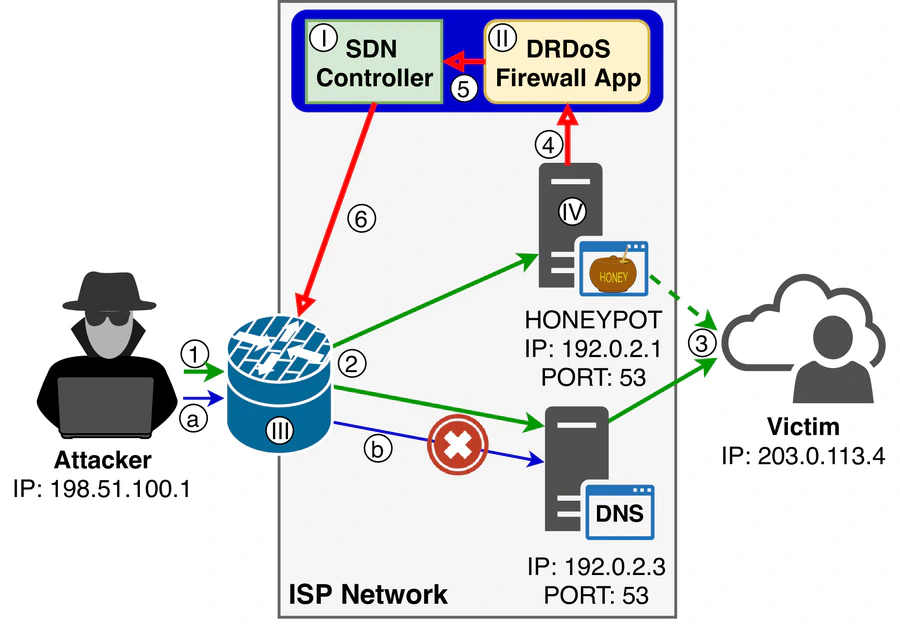
A method for reducing unwanted data traffic in a computer network due to a Distributed Reflection Denial of Service (DRDoS) attack. The method comprises operating a filtering module in a normal mode or a blocking mode to allow or block requests from being communicated within a computer network in response to data from a honeypot device in the computer network. The method allows the honeypot device to continue to monitor further attack requests that are received during the DRDoS attack.
Type
Publication
US Patent US11206286B2